Following on heels of the popular and amusing “The Art of Peering: The Peering Playbook”, this paper describes some of the economics of the Internet Exchange (IX) business along with tactics in use in the industry to build and maintain a critical mass of IX participants. These tactics are presented in a form similar to Sun-Tzu’s “The Art of Warfare ”, the first known treatise on organized warfare.
We introduce the “Startup Hump”, which in the early stages of an IX development presents to most difficult challenge: How does an IX attract NSPs when there is no one there to peer with? We present a theoretical framework that quantifies the value of the IX and its comparative position in the Peering Ecosystem, along with a specific dozen tactics seen in the field whereby IXes launch and get over the “Startup Hump”, whereby IXes attack the dominant IX, and tactics used to defend the IXes position by maximizing the value of the IX.
There are several hundred Internet Exchange Points around the world operating basically the same business; to facilitate the peering interconnections of Network Service Providers. (Note that in this paper we will refer to Network Service Providers (NSPs) to refer to Internet Service Providers and Large Scale Network Savvy Content Providers those that manage their own connectivity to the Internet with peering arrangements.) These peering relationships are often accomplished either public peering (over a shared peering fabric such as Ethernet) or private peering relationships at an Internet Exchange Point.
Definition: An Internet (IX) is a layer 2 service to facilitate the interconnection between Internet Service Providers and Large Scale Network Savvy Content Providers.
In selecting an Internet Exchange Point for Internet Peering, an ISP must determine which ISPs it would like to peer with and which exchange point(s) facilitates those interconnections. In other words, the ISP seeks the IX with the greatest peering value, and one where the value of peering at the IX is greater than the cost of peering at the IX. The costs of peering at the IX includes monthly transport costs into the IX, IX Fees and collocation fees along with Capital (equipment) costs and operations costs for configuring, deploying and maintaining the peering infrastructure.
The ISP must compare also the cost of peering against the cost of transit, a metered traffic fee that has been dropping in the past few years. To do this comparison between peering and transit the NSP must average the monthly traffic volume per monthly cost, against the same traffic simply being purchased from a transit provider. This math is documented more fully in previous research work, “The Business Case for Peering”.
Observation: The Internet Exchange Points exhibit the characteristics of what economists call the “Network Externality Effect”; the value of the product or service is proportional to the number of users of the product or service .
Internet Exchanges are a special case of this effect; the value of an Exchange Point is not the number of participants but a slightly more complex calculation including the number and uniqueness of the routes and volume of traffic peered. Since the value of the IX to an ISP is proportional to the amount of traffic the ISP can exchange in peering relationships at the IX, the value of the IX to the peering population follows the network externality graph as shown below.

On the Y-axis we see the value of the Internet Exchange Point. On the X-axis we see the independent variable that causes the value of the IX to increase; we will use the number of participants for now; as more participants connect to the exchange for peering, the more value an NSP could derive from peering at the IX
All Internet Exchange Points go through the following growth curve. They start out with zero or a few founding ISP members, and face the challenge of attracting additional peers into a building where there are not many peers to peer with. This is the "startup hump", and solutions to this problem were shared with the author in "The Art of Peering: The IX Playbook".
Once the IX reaches critical mass, where the value of participation exceeds the cost of participation, the a well positioned IX experiences exponential growth.
We will use analysis graph for comparing IXes so let’s walk through the stages of IX development to highlight a few key points on the IX value curve.
Sources and Notes ...
Sun-Tzu :The Art of Warfare”, translation by Roger Ames, Ballantine Books, and the on-line version at http://www.chinapage.com/sunzi-e.html See http://www.ep.net/ for a selection of IXes sorted by continent. See also http://www.euro-ix.net/ for valuable IX information and http://www.euro-ix.net/NSP/choosing/list/ for a selection of European IXes. A more detailed description of this effect is available at http://en.wikipedia.org/wiki/Network_externality
Observation: The Startup Hump is the most difficult problem an IX faces.
When the first NSP connects to an exchange point, there is no one else to peer with! How does an NSP justify the costs of attaching to an IX where the cost of participation are so much greater than the value derived from participating? From the IX perspective, how does an IX Operator convince the first NSPs to join its IX when the cost of participation is greater than the value of participating? This is the essence of the “Startup Hump”, the most difficult problem an IX faces. We will present a handful of strategies IXes have been employed to deal with this.
At some point, when enough NSPs connect to the IX, the value of the IX grows to exactly equal the cost of participation; a point called the “Critical Mass” or the “Inflection” point. Beyond this Critical Mass point, the IX can experience exponential growth, as the value is (potentially far) greater than the cost of participating.
When the IX reaches the capacity of the IX (when there is no more collocation space, when the switch has reached maximum port density, when back plane capacity is reached, etc.) the value of the IX levels off. No additional peers can join the IX, but existing NSPs can expand the capacity of their interconnection with others at the IX. These two factors offset each other to level off the maximum value of the exchange marked Vcap.
Unique Networks. We stated earlier that the value of the IX is proportional to the number of participants, but this is not precise. Not all peering NSPs are created equal. The NSPs that build into IXes to save on transit fees do so with the intent to peer with other NSPs that they don’t already peer with. Therefore, it is also important to capture the notion of Available Unique Routes at the IX. We use the Venn diagrams below to capture the unique routes available at an IX, ones that are not available at a competing IX:
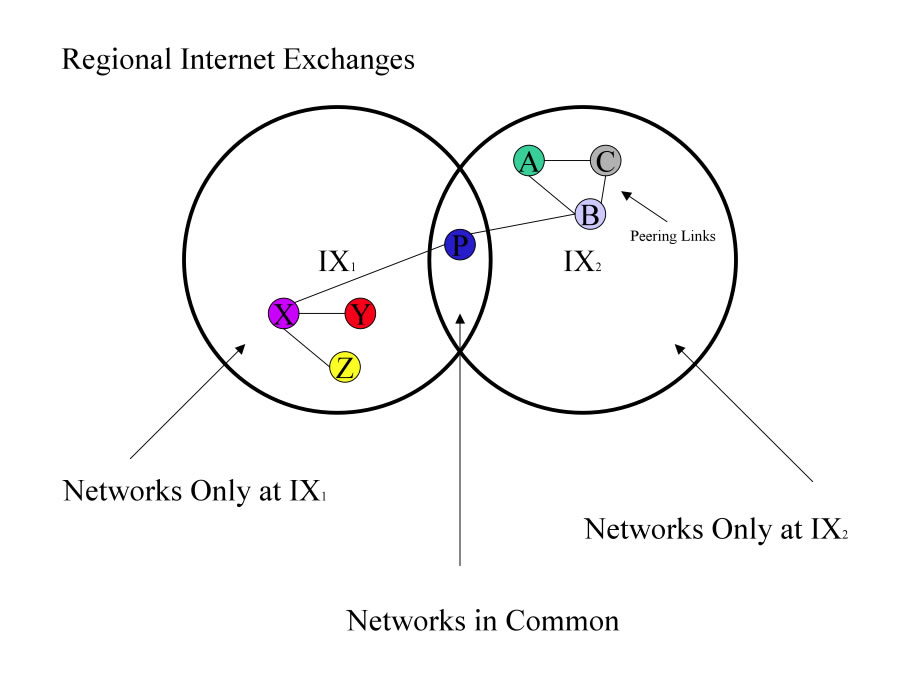
Figure 2 - Venn diagram showing IXes competing, overlapping areas show routes/networks in common at both IXes.
Some IXes make and maintain a competitive intelligence map based on customer discussions and publicly available IX Participants list as shown below. This can be very helpful in strategic targetting and enticing key players -- identifying target ISPs that might benefit from peering even at low levels of traffic.
| Peering Company | Region 1 | Region 2 | Region 3 | Region 4 | Region 5 | Region 6 | Region 7 |
| ISP1 | IX1, IX3, IX5 | IX2 | IX10 | IX6 | IX8 | ||
| ISP2 | IX1, IX5 | IX2 | IX7 | ||||
| IXP3 | IX3 | IX9 | IX10 | IX6 |
Unique routes are a critical differentiator between IXes competing for the same customer in an interconnect region. The calculation of how much traffic and therefore how much money will be saved is based upon the population at the IX, and specifically the amount of incremental peering traffic the prospective customer could picked up at the IX. This leads to another challenge IX Operators face.
The Exchange Point Operator is in a unique central position in the Peering Ecosystem.
The Exchange Point Operator Dilemma: The Exchange Point is well positioned to facilitate the introduction and interaction between service companies, but has no direct and inherent visibility into the services offered or to be offered.
“You don’t know what you don’t know.” Exchange Point Operators, particularly ones starting out without the background, do not know that they do not know enough about the business.
The imperative: the IX must develop and evolve interconnect services with the community of current and future service leaders.
Observation: IX Operators don’t know what they are doing .
This is of course stated provocatively. In a fundamental way, IX operators do not have the information needed to quantify to a prospective ISP the value of their service. Generally, NSPs do not share openly
The IXes don’t have the ability, the desire, or are forbidden from tapping into the route announcements on public switches or across private cross connects to determine the value of the traffic exchange. This information is considered proprietary by many NSPs but essential to the calculation of value to the NSP. Further, if shared, this information could help the IX support charging a higher price given the higher value derived from participation. For these reasons, IXes are often kept dumb with respect to the value of the IX to ISPs. But, as we will see, this problem can be mitigated to some extent with the help of the peering population.
Observation: The average value of an IX can be calculated empirically.
How much is an Internet Exchange Point worth on average to the participating ISPs?
To estimate the aggregate value of an Internet Exchange Point to its participants we can calculate the alternative cost of traffic exchange should it have to traverse transit links.

For example, in 2003 the London Internet Exchange averaged about 20 Gigabit per second of traffic exchanged among members. If we assume that this traffic would otherwise have been exchanged through an upstream transit provider that charges $100/Mbps, the LINX is saving the participants $100/Mbps * 20,000 Mbps = $2,000,000 per month. There are 135 members participating in the LINX, so this works out to $14,814 per member. If we assume that each member pays membership fees , GigE port fees, collocation fees, etc. of about $2500/month in costs, it is easy to see why the LINX members are supportive (and in fact protective) of this IX . As shown in the IX Value Curve below, the average participant value of the LINX ($14,814/month) is so much higher than the cost of peering at the LINX (~$2500/month)!
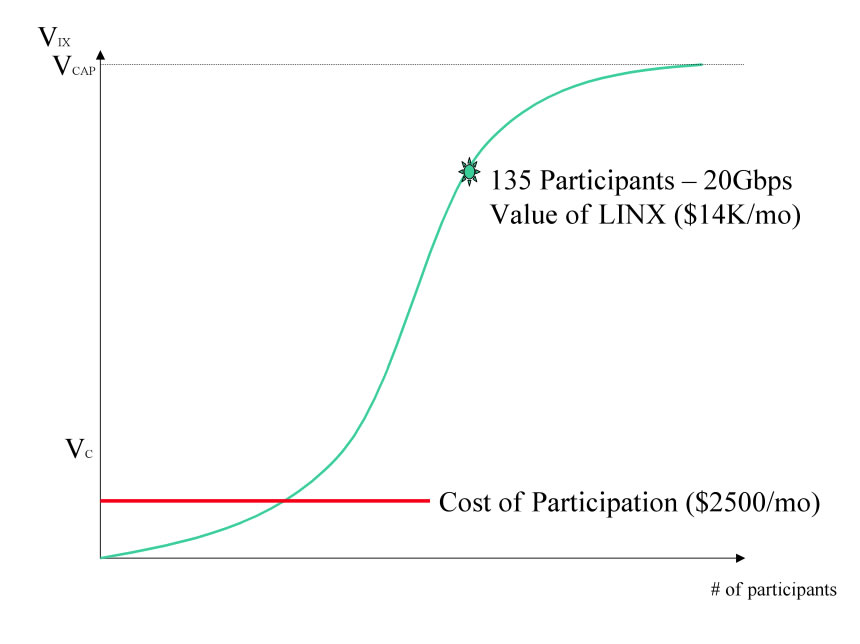
Figure 3 - The average value of the LINX
This is a significant and defensible competitive advantage, and the gravitational pull continues to grow as more NSPs and more peering traffic becomes available at the IX. These benefits though are only available after the IX gets past the Startup Hump.
Now that we have laid out the groundwork, we will explore the battlefield and maneuvers employed as the IXes compete with each other in the marketplace.
Sun Tzu said: The art of war is of vital importance to the State. It is a matter of life and death, a road either to safety or to ruin. Hence it is a subject of inquiry which can on no account be neglected.
In earlier research , NSP were asked “How many IXes are needed or are desirable in an Interconnect region?” The general answers were either one or two, that three or more tend to fracture the peering community who then must determine which one(s) they will go to get which subset of the available routes in the region .
Today there are many Interconnect Regions with multiple competing IXes. For example, consider the competing exchanges in the table below.
| REGION | IX1 | IX2 | IX3 |
|---|---|---|---|
| Chicago | AADS | EQIX-Chicago | MAE-Chicago |
| Washington, DC | PAIX-Vienna | Equnix-Ashburn | MAE-East |
| Tokyo | JPIX | JPNAP | NSPIXO2 |
| London | LINX | LoNAP | MANAP |
In Tokyo, NSPs choose between the JPIX, JPNAP, NSPIXP2 for domestic peering. If we use the # of participants as the value determinant, we see these IX value curves drawn below :
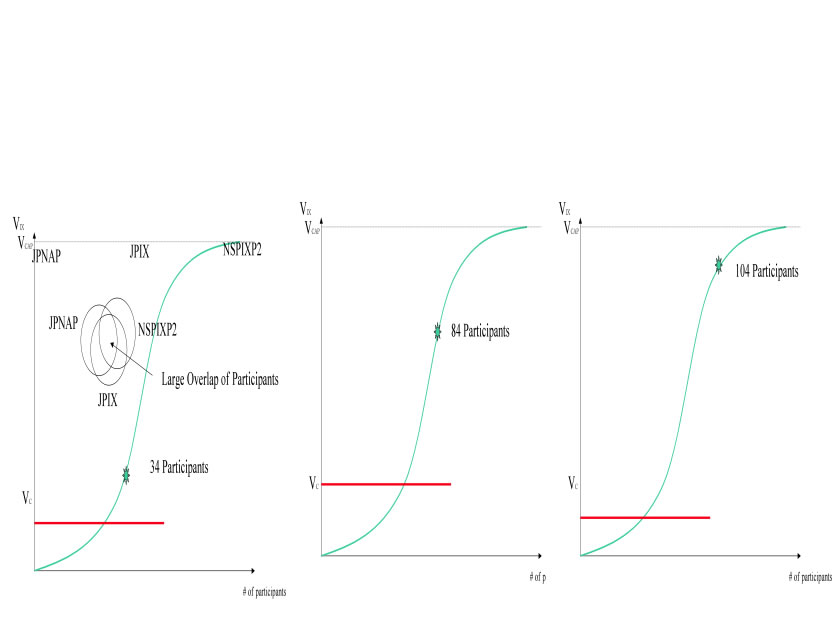
Figure 5 - Network Effect graphs of JP Ixes
In most Internet Regions there is at least one “Dominant” Internet Exchange, and in many cases there are one or more that compete with the Dominant IX. As more NSPs join this IX, the dominant IX provides even greater value to all of its participants, a “gravitational pull” leading to a increased momentum of customer growth. The dominant IX enjoys substantial leverage in the market for IX services.
Note however the comparison of IX curves includes both the cost function and the value function. In 2001-2002 when Equinix Ashburn was competing with MAE-East for dominance in the Washington D.C. area, the cost of the ATM MAE-East service was used representing a significant barrier to peering when compared against the Equinix Ethernet and PAIX Ethernet peering solutions . The calculated value to the participants was substantially higher when the cost of the ATM circuits and equipment was taken into account as shown below.
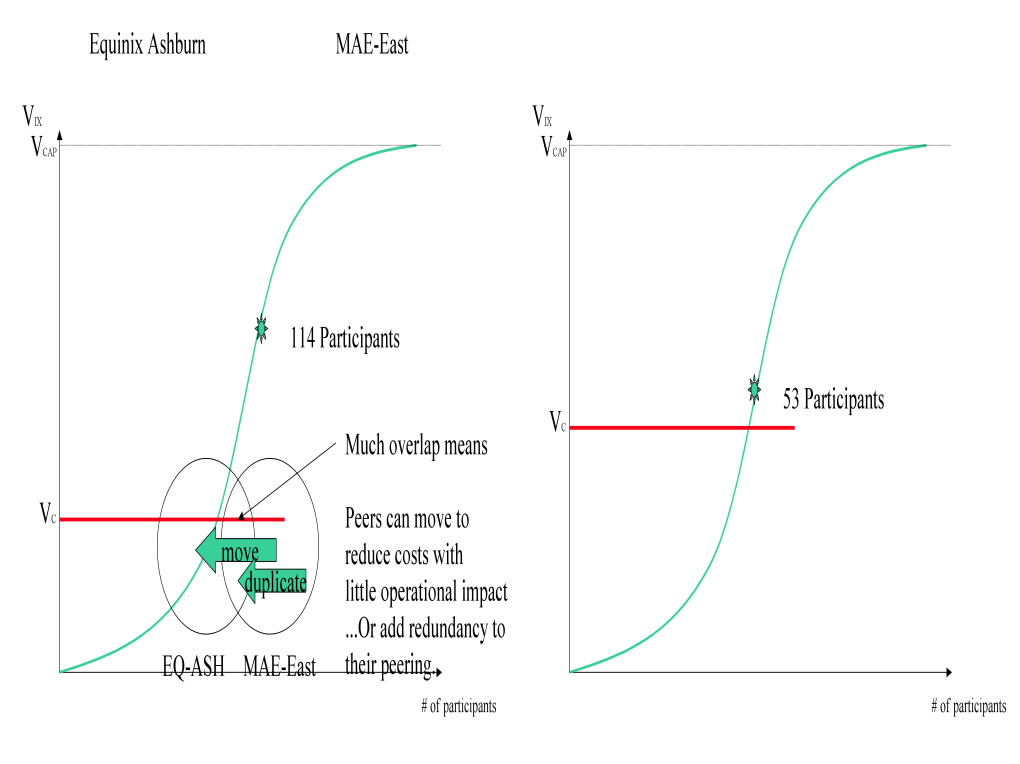
Figure 6 - EQ-ASH vs. MAE-East
These examples were drawn out to illustrate that these competing IXes look similar to warring parties:
For these reasons we will present the observed tactics deployed by IX Operators in military terms following the development stages of the IX; from the StartUp hump maneuvers, to attacking the dominant IX through defending a dominant position..
Sources and Notes ...
“In battle, there are not more than two methods of attack--the direct and the indirect; yet these two in combination give rise to an endless series of maneuvers.”
The dominant IX of course has a stronger peering population and therefore a greater gravitational pull. A rational NSP will generally prefer the IX with the most peering value for the ability to offload the most incremental peering traffic. There isn’t much more to the IX business value proposition than that, and there are relatively few tactics that are used to influence this dynamic to build a strong and sustained critical mass of peering traffic.
The following section details a handful of tactics for overcoming the “Startup Hump. These can also be used for more well established IXes looking to gain ground quickly. These maneuvers have been seen in the field and are based on conversations with IX Operators over the past five years.
It is assumed in the following “Startup Hump” tactics that the IX has the ability to support discriminatory pricing. Some membership-based organizations may not be able leverage these tactics since they require that the same fees be charged to all members.
“On contentious ground, I would hurry up my rear.”
When there is not enough value in the IX to attract NSPs, an IX operator must do what is necessary to find a reason for NSPs to join. One approach is to reduce the cost of peering for early adopter NSPs to entice them into participating. This tactic is shown graphically below. With this approach it will take fewer peering session, less traffic, and in general less justification for NSPs to build into the IX.
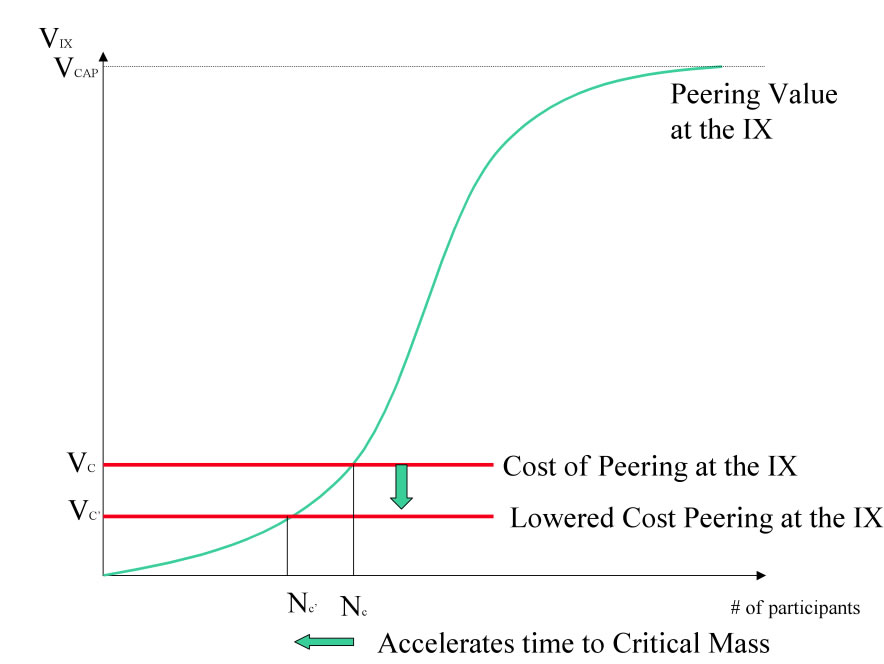
Figure 7 - Lowering Peering Costs to get over the startup hump
Note that there are some costs of peering within the control of the IX Operator, and some that are not. An IX Operator can certainly make a free port available for peering and even help cover the costs of collocation for some time, but the NSP generally has to pay for the peering equipment. Therefore, there is still a cost that needs to be justified, and this cost is often justified with one of the following:
Lowering the cost of peering has the following Benefits and Drawbacks:
| Benefits of Lowering Peering Costs | Drawbacks of Lowering Peering Costs |
|---|---|
| Easy to do | Little or no revenue |
| NSPs Name available to help promote IX (hopefully) | Expectation from customers of perpetual free service |
| The price can be renegotiated at the end of the contract | Value may be perceived as low since the service is free |
| Easier for customers to justify participation |
If the promise of peering value is not sufficient to attract key peers (those with name recognition, unique routes, “Open” peering inclinations, large volumes of traffic available for peering, etc.), added incentives can be used to bring these select players in.
For example, in 1999 Equinix issued warrants for stock to WorldCom to help offset the cost of and expedite the building in carrier and Internet Service bandwidth. WorldCom could then participate in the upside as the stock appreciated as a result (in part) of WorldCom’s participation .
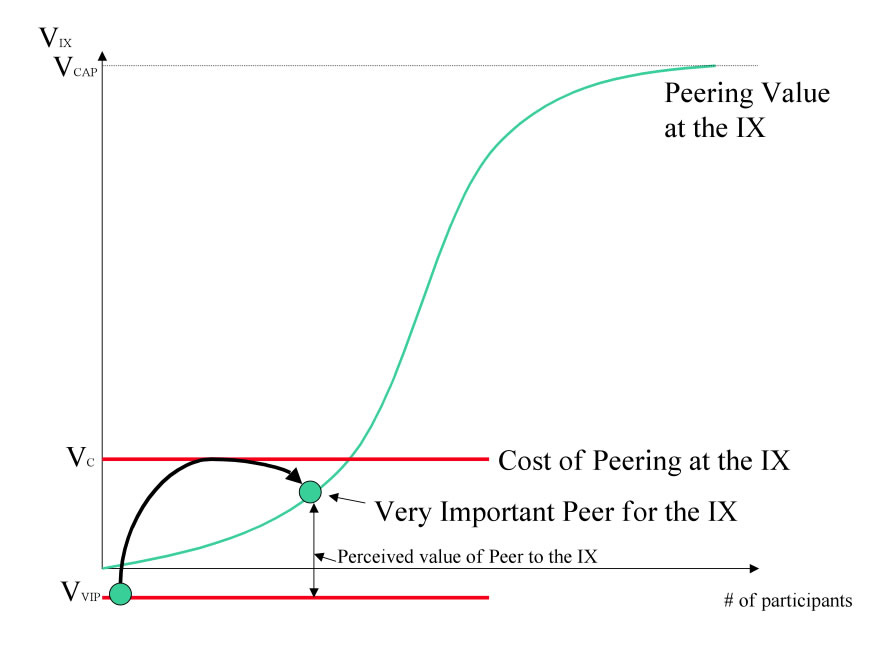
Figure 8 - Buy in key peers
When considering this option one needs to calculate the cost to “buy in” the participant and estimate the value of their participation. Will they peer openly? Will they allow their name to be used to draw a peering crowd? Also, one must manage the perception of their peers; the peers that may otherwise believe that too should participate in the upside for participation. Finally, one needs to consider how long the IX can wait to pull these players in by natural gravitational forces.
Military tactics are like unto water; for water in its natural course runs away from high places and hastens downwards.
An emerging IX can leverage the natural tendency for NSPs to buy only if the value exceeds the costs. Specifically, an emerging IX can not charge the same fees as a dominant IX without providing a corresponding value. All things considered equal, the NSPs will simply choose the IX with the higher peering value. The notion with value-based pricing therefore is to charge a monthly fee that is proportional to the benefit derived by participation, and this can take one of two forms.
For the low end of the market, the IX can make the peering participation fees very inexpensive (or free as at the NAP of the Americas) and metered. This way the IX can reduce the hurdle to peering at the IX to the point where it makes sense. For example, as shown in the “Metered Cost” line below, an IX can include free peering ports with a metered rate (like $10/Mbps) for peering port use. This allows the lower end of the peering spectrum easy entry into peering, which collectively can build a large population of low volume peers that may help attract additional peers to the IX.
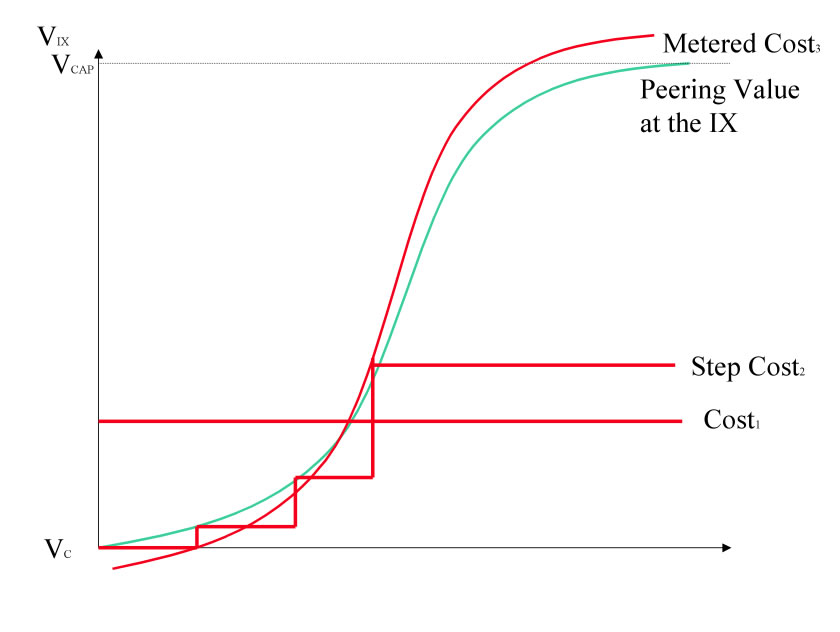
Figure 9 - Price Peering Proportional to Value
A second approach is to price the ports on the switch based on the number of NSPs attached. The first ten ports would be heavily discounted (say 60%), the next ten less discounted (say 40%), and the next just below market rates (say 20%). Once above the “critical mass point” is reached (where the cost is justified), contracts can be adjusted upwards to or above market rates.
Ultimately these methods price proportionally to the value derived to the customers and help speed the growth of the peering population.
“All war is based on deceit ”
Observation: There is a range of deceit in the IX business.
Bluff Carriers. Frustrated IXes dealing with the Startup Hump often employ tactics to signal greater value to peering prospects. Paul Vixie at an APRICOT conference in the late 1990’s described the StartUp phase of the PAIX; they needed to persuade the large carriers to build in to the PAIX facility in downtown Palo Alto. Pacific Bell was contacted and told that WorldCom was generating significant revenue from the PAIX population and that the customer base would like a choice in carriers. Not wanting to give up business to WorldCom, Pacific Bell built into the PAIX. WorldCom of course was not in the building at the time, but when Pacific Bell showed up and started selling capacity, WorldCom was contacted to come in and compete. Once these two carriers were in the building, the population of carriers and NSPs was able to grow.
Bluff two potential peers. These same tactics have been used by some IXes to attract customers in; identify potential peers that the prospect would like to peer with and signal they are there or “pretty close” to installing. The prospects desired potential peers are then also targeted with the same type of signaling in the hope that neither NSP will realize that the other wasn’t already installed at the IX. This tactic often fails, as the peering population is a tight knit group of professionals that talk to each other for a living. These IXes lose credibility and it becomes more difficult to build sufficient trust to build momentum out of the startup hump.
Misleading Customer Lists. Another form of this broadly seen across the IX industry is the misrepresentation of the Peering Participation on the website. The NAP of the Americas (NOTA) for example has a “Representative Members” list to imply the peering population. The NOTA was developed by a consortium of NSPs and carriers, and this consortium list was used in the early days to signal support for the NOTA but implied participation. As a result, some NSPs were led to believe there were more participants in the NOA than there were.
These misleading tactics are unfortunately common in the IX community, particularly those that are struggling through the start up hump. If there is no value to participation then one has to sell a vision, paint a compelling view of the future of the IX. Scraps of interest are sometimes crafted into “marketing speak” in the form of “backed by” or other such words. The problem is the “well-chosen marketing speak” is often repeated without the same precision by the sales people, leading to charges of misrepresentation, etc.
“On open ground, do not try to block the enemy's way. On the ground of intersecting highways, join hands with your allies.”
“We cannot enter into alliances until we are acquainted with the designs of our neighbors.”
When @Home went bankrupt it left in its wake a dozen or so cable companies that were left to find Internet service for their customers in thirty days! Very quickly they learned that transit was very expensive particularly as the file sharing (Kazaa, morpheus, Napster at the time) was consuming 40% of all available transit bandwidth . The author spent time getting acquainted with this community to find a clear and compelling aligned interest – they each could save millions of dollars per year if they interconnected their networks together in peering relationships at an IX.
As a group, the North American Cable companies converged on an IX, providing that IX with a huge gravitational pull. The cable companies were “Open Peers” so, generally speaking, were willing to offload as much traffic as possible with NSPs and content companies interested in peering. This group buy-in tactic helped build a strong critical mass and increase the value for the IX populations in which they participated. This is shown graphically below and can be a very effective start up tactic.
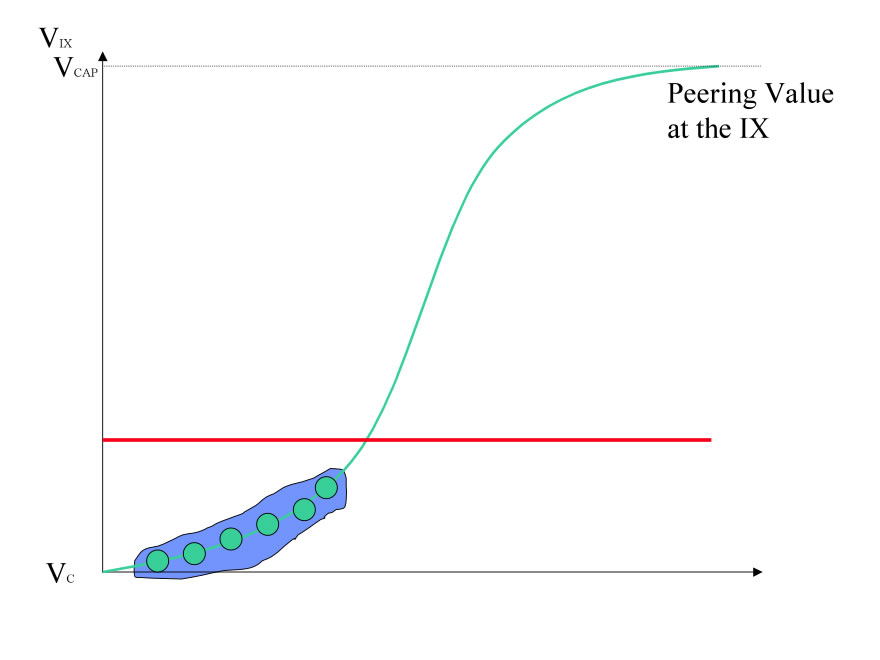
Figure 10 - Group Buy in to IX
In Europe this tactic was also seen in another form; most European IXes were started by a group of NSPs. They organized as a formal association, with support for shared peering services and organizational oversight in return for founding member participation. This en mass adoption of an IX is also an effective way to build the IX quickly to critical mass.
If he is secure at all points, be prepared for him. If he is in superior strength, evade him.
Regardless of the size of the peering population at the sub-dominant IX, there are usually unique networks only available at the IX. These “unique networks” have a vested interest in increasing the peering population at the IX they selected and may be willing to share traffic information necessary to attract and build the IX population.
Specifically, this tactic involves pursuing strategic relationships between the IX and the NSP community to share prioritized lists of peering targets and measured traffic levels should the NSP peer at the IX. Armed with this information, business cases and compelling pricing can be constructed to attract these “key peers” into the IX, perhaps away from or in addition to the dominant IX. This can have a flywheel effect as these companies then can share their information to further accelerate the build up at the IX.
When the dominant IX population is strong, a sub dominant IX may need to attack the dominant IX where they are weak, presenting reasons to select their alternative IX that do not involve the population. Seen in the industry , these weak point might include:
The Leverage Differentiated Services tactic can best be diagramed below.
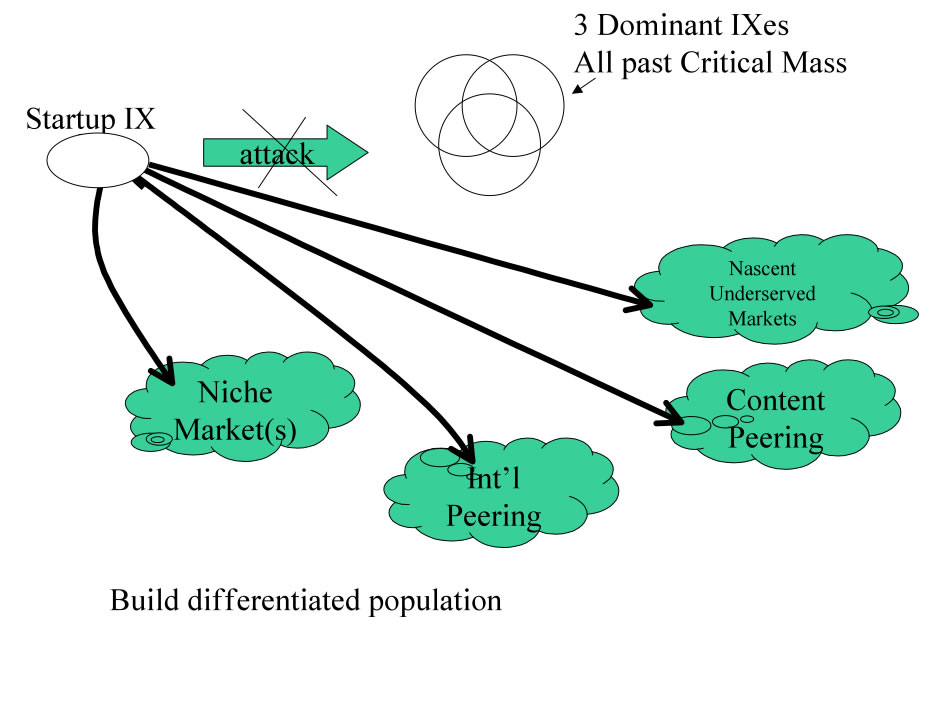
Figure 11 - Evade and attack weakness
Once the IX population is built up, this tactic can then be followed by the divide and conquer tactic described next.
“If the enemy leaves a door open, you must rush in.”
When IX participants are sparsely peered, they are vulnerable to moving. When the IX participants are unhappy with the quality of the peering service, if they have suffered from outages or decreased value provided by the IX, they are vulnerable to moving. This tactic requires an IX identify those vulnerable participants and their current and desired peers. Next the IX identifies how much peering traffic is being exchanged and calculates the value derived from participation at the existing IX. Those with few peering sessions, those with small amounts of traffic exchanged, are deriving the least value and therefore may be willing to provide details of who they would need to peer with in order to be worthwhile to move. These existing and desired peers can then be approached and brought through the same process, possible in a group buy in tactic. This tactic rarely however succeeds in mass migrations due to the “Operations Gear Tenet ” but often yields incremental adoptions for redundancy and future expansion. NSPs not receiving the value from the IX that they expect can be powerful advocates for other potentially interested in moving and can also provide a great wealth of Intel on the competitive landscape.
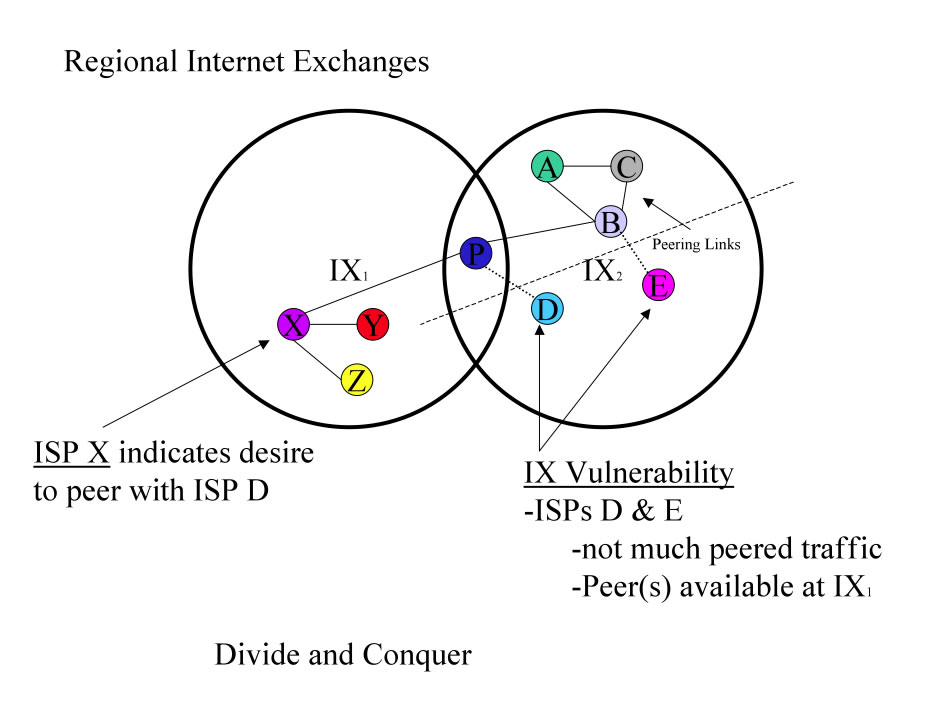
Figure 12 - Divide and Conquer
In respect of military method, we have, firstly, Measurement; secondly, Estimation of quantity; thirdly, Calculation; fourthly, Balancing of chances; fifthly, Victory.
The IX business is unique in that the value provided is out of the control of the IX operator. Whether an NSP will peer, and if so how much traffic will be exchanged, and if that peering will last for the duration of the IX contract, are examples of variables that are part of the value of the IX calculation but outside of the control and sometimes even outside of the visibility of the IX Operator. Many NSPs consider peering relationships, traffic volumes and projections, etc. proprietary and confidential. This makes gathering intelligence about the value of the IX service and the desirability of the IX very difficult to obtain. It makes collection and management of the Intel that is available even more important.
Observation: Only one half of a peering relationship needs to be exposed to determine a peering relationship.
Observation: Ninety percent of Intel is delivered through informal channels.
Valuable Intel includes
Intelligence gathering requires constant reconnaissance missions. This includes travel to and speaking at networking conferences and particularly forums that attract NSPs and peering coordinators. Of particular interest are:
With this information opportunities are made available and vulnerabilities in the competition are made available. The appropriate meeting at the appropriate time armed with the appropriate information can make or break an IX. These behind the scenes tactics are sometimes referred to “Guerilla Marketing.” An IX that fails to execute successfully here is flying blind, will learn of opportunities late or never, and is vulnerable to being blind sided.
IXes with multiple exchanges in difference areas can leverage a well populated IX to build critical mass in other locations. For example, if the dominant IX in one region is the top seller (since the value is greater than the peering costs) one can bundle a port in a less populated region for a collective discount.
Another version of this was seen when MFN owned the PAIX and bundled in free PAIX ports and rack space with larger fiber deals . The PAIX has also successfully pulled together and leveraged multi-site deals independently.
Interconnections are the glue that makes it difficult for NSPs to leave an IX. Customers would have to duplicate these sessions elsewhere (or cancel them), which is difficult to do since the populations at IXes are very different.
Definition: Stickiness refers to the forces keeping an NSP at the IX.
Observation: There are several forms of stickiness; value-based, time-skew based, and interdependence-based stickiness. Next to getting over the Startup hump, building and maintain population stickiness is the most important IX activity.
Value-based Stickiness. As seen in the previous example with the LINX, on average, the value of participation is far greater than the cost of participation. This financial benefit makes it very difficult for an ISP to leave.
Time-Skew-based Stickiness. One tactic to increase stickiness is facilitate time skew in peering and service subscription. An NSP purchases IX and collocation services for a period of time and uses the services to exchange traffic in peering (and possibly transit) relationships. The degree to which these services no not overlap is the degree to which time skew increases stickiness; there would be some pain to pull out midway through one contract, midway through a transit contract, midway through a customer transit relationship, etc. If all contracts and peering relationships terminated at the same time, there would still be the operational pain and unavailable for service time while picking up and moving operational gear elsewhere. Generally speaking, there would be great disruption to move out of a collocation center or disconnect operational gear. It is worth restating the Internet Operational Gear Tenet.
“Operational Gear rarely gets disconnected.”
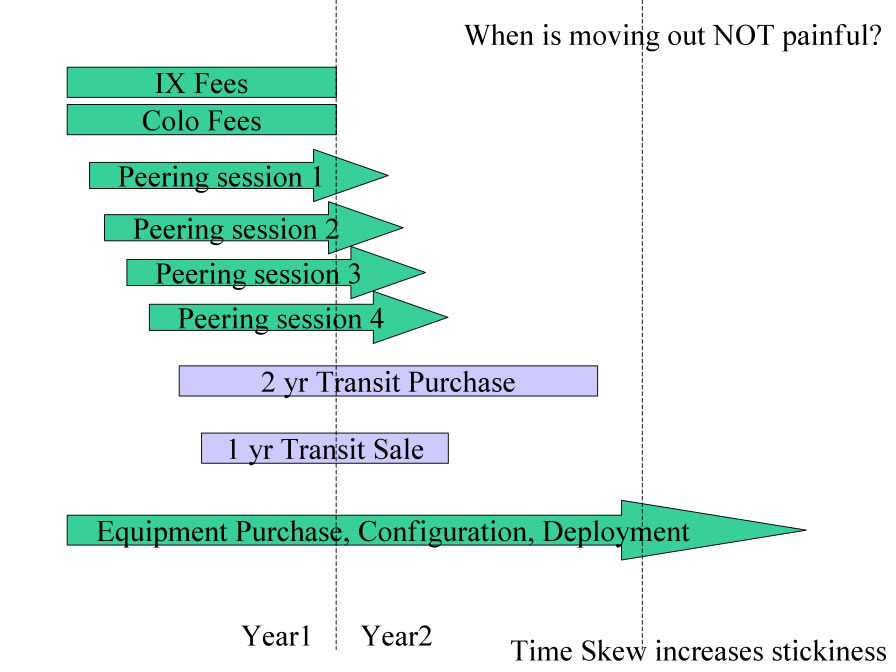
Figure 13 - Time-Skew-based Stickiness
Interdependence-based Stickiness. but perhaps more important dimension of stickiness is inter-provider interdependence. More interconnections (whether peering or transit) indicate more interdependence among participants. This is the glue that keeps participants from moving; to do so they would need to invalidate the interconnection or coordinate with the other parties to pick it up elsewhere.
Also, the more interconnections, the more value derived by the participants. As the value of the IX to the participants exceeds the cost, the benefits of staying start to far outweigh the costs of participation, even through periodic major disruptions .
Here are several methods of increasing interdependence among the IX population:
Benefits of these tactics:
Ultimately the goals here too are to build a community of peering coordinators that see value interacting with the IX, more than just paying fees for participation. The IX that helps the NSP maximize their value of the IX is less likely to lose customers and may very well help steer additional customers to that IX. Further opportunities (other site deployments, new business offerings, etc.) are also made known to the IX that interacts with the community more, and more intel is shared directly or indirectly with the facilitating IX.
In Europe, the defense system is automatically in place; if a rival IX approaches a founding member of the dominant IX, little more than intelligence gathering for the dominant IX is accomplished. Founding members are unlikely to move from “their” IX, although they may be persuaded to add a presence elsewhere if a compelling reason is given.
For commercial IXes, it is critical to work very closely with the peering community to build and maintain its peering population. Specifically, beyond understanding the customers business , it is critical to understand their peering inclinations . Armed with this intel, an IX can facilitate peering and effectively manage introductions to maximize the degree of interconnection. This information can be used to create a peering map as below, highlighting the degree of interconnectedness, or peering value, and maximizing stickiness. Ideally this intel would be expanded to include the competitors peering map.
The Peering map tracks peering sessions . At least on e side needs to share their peering session lists in order to fill in the appropriate square with a peering mark. The goal with this tactic is maximize interconnectedness, to maximize peering and thus maximize the value and as a side effect information flow through the IX Peering Manager. Let’s take a look at the peering map.
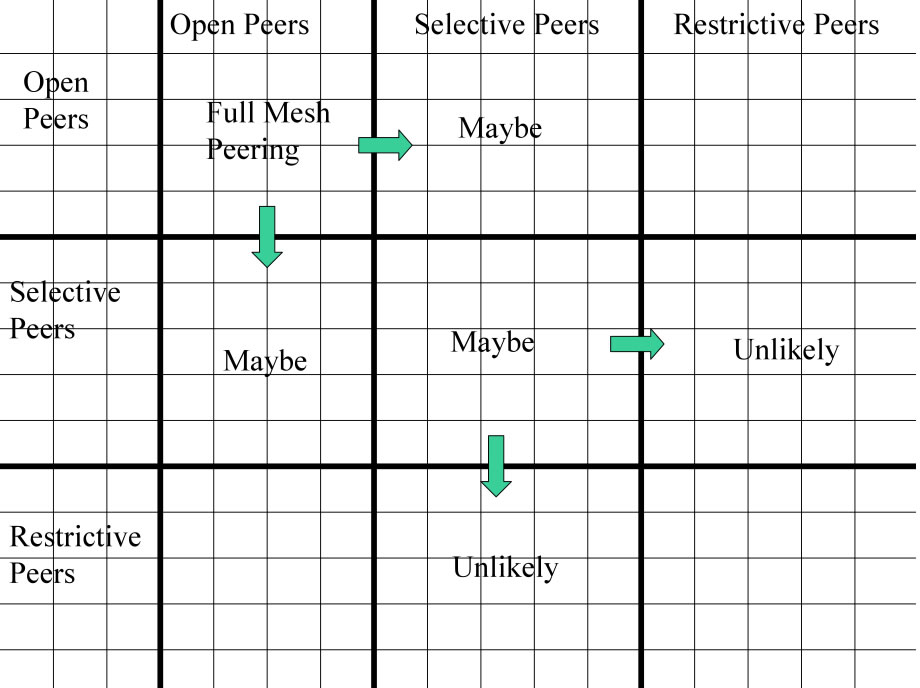
Figure 14 - Peering Map
From the Peering Map above we can see that a maximally peered IX would have all “Open ” peers peering with all other “Open” peers.
Those NSPs with “Selective” peering inclinations require certain thresholds to be met (traffic volumes, interconnection points, ratios, etc.) and if understood and met, an IX can facilitate introductions leading to peering between some “Open” and “Selective” peers. Selective peers may peer with other selective peers, but their policies need to be understood and articulated before the introductions should be made. Many Selective peers prefer to manage their own peering and are not receptive to peering introductions.
Introductions to “Restrictive” peers are not worth doing since Restrictive peers generally do not want additional peers. Making them aware of Selective peers as they join however may indirectly help facilitate peering between Restrictive and Selective peers.
With the peering map filled in and maintained, the peering policies can be systematically tracked and understood, and an IX Peering Manager can facilitate the introduction of prospective customers to the current peering population, helping to ensure the value growth of the IX. The absence of such peering initiatives is to manage the IX development based on hope and luck.
For example, consider a snapshot of a peering population at a well established IX below. The participants peering are plotted across the X and Y axis, with the intersection highlighting the peering inclination and peering state.
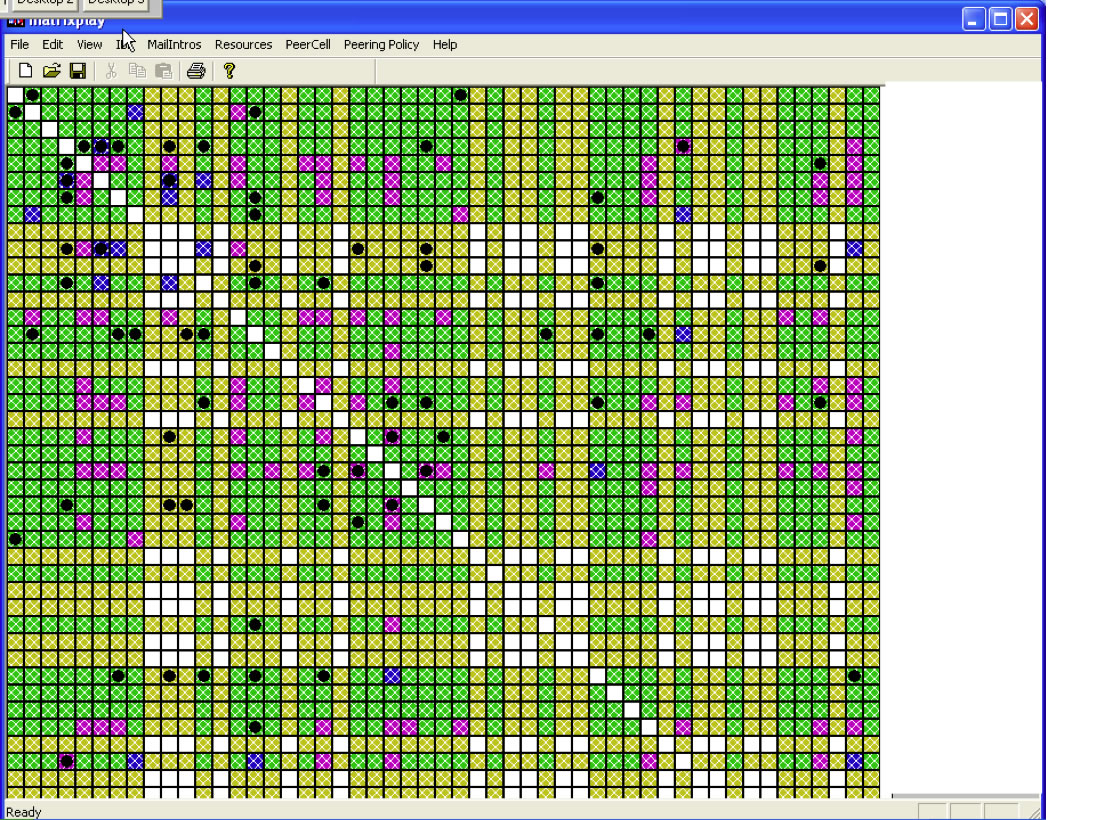
Figure 15 - Sample Peering Tracking Map
Green indicates that both parties have an “Open” policy or have explicitly indicated a willingness to peer with the other party.
Yellow indicates one or the other party has not indicated affirmatively or negatively, either by policy or explicitly, a peering inclination with the other party.
Purple and Blue indicate peering relationships, and black diamonds indicate peering introductions (in person, via conference call, or via phone call introductions have been made.
By systematically tracking and managing the interconnection (to the extent allowed by the population ) an IX can maximize the interdependence stickiness.
Working closely with NSPs to map this
Index of other white papers on peering
WIlliam B. Norton is the author of The Internet Peering Playbook: Connecting to the Core of the Internet, a highly sought after public speaker, and an international recognized expert on Internet Peering. He is currently employed as the Chief Strategy Officer and VP of Business Development for IIX, a peering solutions provider. He also maintains his position as Executive Director for DrPeering.net, a leading Internet Peering portal. With over twenty years of experience in the Internet operations arena, Mr. Norton focuses his attention on sharing his knowledge with the broader community in the form of presentations, Internet white papers, and most recently, in book form.
From 1998-2008, Mr. Norton’s title was Co-Founder and Chief Technical Liaison for Equinix, a global Internet data center and colocation provider. From startup to IPO and until 2008 when the market cap for Equinix was $3.6B, Mr. Norton spent 90% of his time working closely with the peering coordinator community. As an established thought leader, his focus was on building a critical mass of carriers, ISPs and content providers. At the same time, he documented the core values that Internet Peering provides, specifically, the Peering Break-Even Point and Estimating the Value of an Internet Exchange.
To this end, he created the white paper process, identifying interesting and important Internet Peering operations topics, and documenting what he learned from the peering community. He published and presented his research white papers in over 100 international operations and research forums. These activities helped establish the relationships necessary to attract the set of Tier 1 ISPs, Tier 2 ISPs, Cable Companies, and Content Providers necessary for a healthy Internet Exchange Point ecosystem.
Mr. Norton developed the first business plan for the North American Network Operator's Group (NANOG), the Operations forum for the North American Internet. He was chair of NANOG from May 1995 to June 1998 and was elected to the first NANOG Steering Committee post-NANOG revolution.
William B. Norton received his Computer Science degree from State University of New York Potsdam in 1986 and his MBA from the Michigan Business School in 1998.
Read his monthly newsletter: http://Ask.DrPeering.net or e-mail: wbn (at) TheCoreOfTheInter (dot) net
Click here for Industry Leadership and a reference list of public speaking engagements and here for a complete list of authored documents
The Peering White Papers are based on conversations with hundreds of Peering Coordinators and have gone through a validation process involving walking through the papers with hundreds of Peering Coordinators in public and private sessions.
While the price points cited in these papers are volatile and therefore out-of-date almost immediately, the definitions, the concepts and the logic remains valid.
If you have questions or comments, or would like a walk through any of the paper, please feel free to send email to consultants at DrPeering dot net
Please provide us with feedback on this white paper. Did you find it helpful? Were there errors or suggestions? Please tell us what you think using the form below.
Contact us by calling +1.650-614-5135 or sending e-mail to info (at) DrPeering.net